In 2019, cross-site scripting has been identified as one of the most common cyber security threats. Nearly 40% of all cyber-attacks were due to XSS vulnerabilities. A lot of web giants such as Google, eBay, Facebook, and Twitter have been affected by cross-site scripting, so it’s not a new cyberthreat.
Our guide today focuses on how to prevent XSS attacks, as we will show you everything you need to know about cross site scripting. You’ll have a better understand of how XSS works and how to keep your website secure.
What is XSS?
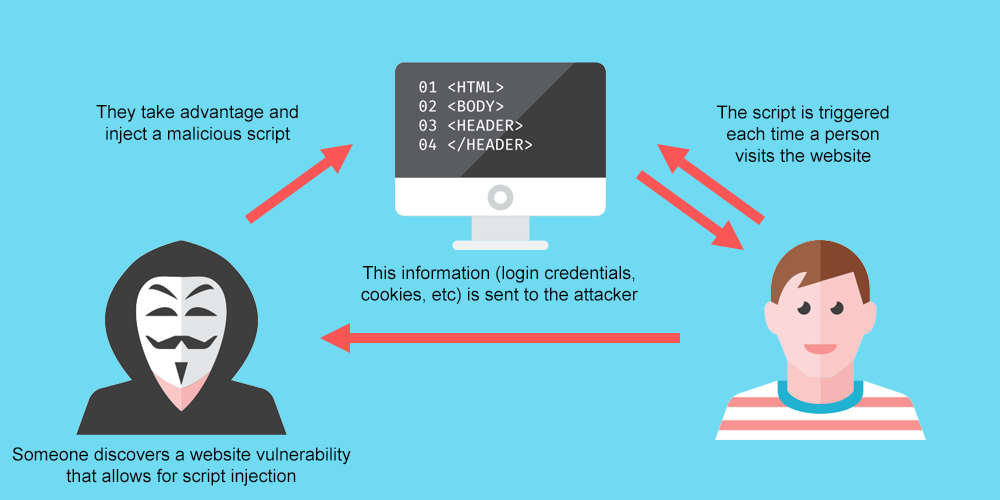
Cross-site scripting is the type of cyber attack where malicious scripts are injected into trusted and credible websites.
These types of attacks are possible in Flash, HTML, CSS and ActiveX. JavaScript is known as the most common target of cyber criminals as it’s essential to most browsing experiences. Most sites which are larger and interactive were built with JavaScript. It’s so popular amongst the website community as it allows you to do virtually anything on the website. And this is exactly where the problem lies. Cyber criminals use JavaScript to login to the back of your pages and insert any type of malicious script.
How does XSS work?
Cybercriminals perform XSS attacks on WordPress in two ways. They take advantage by either user import or bypassing the same origin policies.
Manipulating user input
This is the most common ways in which XSS attacks are being performed. In most cases WordPress sites have user input fields, such as comment forms, search bars, contact forms, and login pages. The import field is enabled by JavaScript a powered plugin or an active theme.
The problem is that not all themes and plugins are 100% secure and a lot of them have XSS vulnerabilities. Which is why cyber criminals can utilize these vulnerabilities in import fields and run malicious software.
It would be best if the user input fields accept only plain text as an input. WordPress, however does have a user input vulnerability, which gives hackers the opportunity to enter an executive code into the input field which is sent to the database.
Bypassing same origin policies
Same-origin policy will restrict a page to retrieve data from other webpages. With this policy, browsers allow scripts which are contained in the first page to access data in a second page if they share the same origin. This will ensure that no cross-site requests will be made.
For example, by using this policy your Facebook page and online banking, if opened in the same browser, cannot share information with each other. On the other hand, if you have multiple Facebook tabs, they can exchange script and sorted out between them.
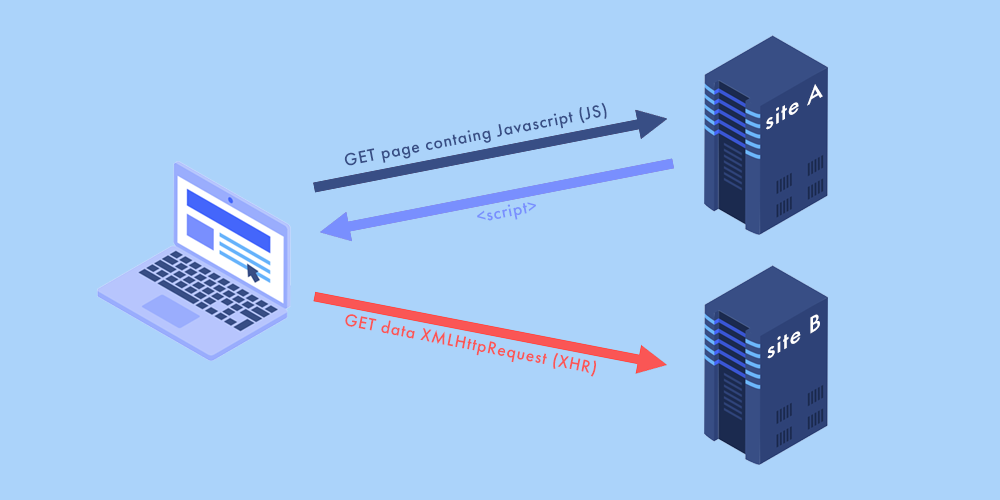
Despite all security measures, cyber criminals have a way around the policy using session cookies. Every time a browser is opened, it will generate a session cookie which will validate you as a website user and does assist you move between pages smoothly.
With the help of session cookies, login credentials are stored, as well as shipment details, credit card information, and other sensitive data. For example, if you wish to login into your online banking, when you open the website session cookie will be generated. If that wasn’t the case, you would need to log into your online banking account every time you want to switch pages.
It’s quite often that users’ browsers have vulnerabilities. In such cases, cyber criminals use code which they inject into the user input and steel session cookies. By using this method, hackers steal cookies of all websites which are opened in the users’ browser. They can use them to login to users account and steal sensitive data.
Is XSS dangerous?
Cross-site scripting is a very common high-risk vulnerability with WordPress. Such attacks are seen often as they can be very difficult to address. Even if you do have build-in protection, it’s very easy to make a mistake which will lead to cross-site scripting. Just one mistake is enough to make your website vulnerable. When hackers find XSS vulnerabilities, they can use that to steal financial data, account credentials, as well as facilitate physical scams. They can get access to your computer remotely or spread computer worms.
Compared to SQL injections, excess attacks are viewed as less dangerous. However, when in combination with social engineering, XSS allows hackers to complete extremely dangerous and advanced attacks, such as keylogging, planting trojans, and identity theft.
To battle against such attacks, a number of large IT companies create special big bounty programs. They are implemented by a lot of organizations and offer recognition or compensation to users who could manage to find XSS vulnerabilities. In this way they invest in cyber security by having outside developers locate their bugs.
How to prevent XSS attacks?
Let’s take a look at some proven ways to prevent these attacks. There are multiple ways you can use to protect your website. If you have advanced technical knowledge, you can simply add code snippets to sanitize and validate using imports. If you, however, are not that technically advanced when it comes to WordPress, it’s better to rely on a professional.
In the meantime, you can use these methods to prevent XSS attacks:
Security plugin
By using a security WordPress plugin, you can ensure the ultimate security of your website. Make sure, when choosing a plugin, that it has the following functionalities: - Regular scans of your website for malware - Firewalls to block any malicious traffic - Capable of implementing WordPress hardening measures - Allowing you to manage all website updates - Backup for your website
Dedicated plugin
By using an anti-XSS plugin you can prevent cross site scripting. These plugins work by blocking parameters which are commonly used in XSS attacks. They provide security for user input fields like login forms, comments, or search bars.
Conclusion
Nearly 39% of all WordPress vulnerabilities are connected to XSS issues. Brands lose millions in trying to battle the consequences of such attacks. In order to avoid them, make sure you are familiar with cross site scripting and all preventive measures.





